
DuoPlus cloud mobile phone has achieved a dual upgrade in "Renewal Management + Batch New Device Creation"
Introduction: In this new era of rapid change, every small shift can lead to new trends in the industry. DuoPlus Cloud …

Many brand owners with a strong online presence and unique products may worry about intellectual property infringement, counterfeit goods sales, and the eventual devaluation of their brand, leading to a decline in sales. In this article, I will introduce you to the biggest threats most companies currently face and provide you with methods to address these threats, including using dynamic residential proxies to perform data collection and implement real-time brand intelligence.
Recent global developments show that COVID-19 or the coronavirus is impacting our healthcare, economy, and even brands. One brand affected by this turmoil is Corona beer. Before the pandemic, this highly successful Mexican brand symbolized fun and relaxation. However, due to the virus’s name similarity to the beer, market research by YouGov found that purchase intent among American consumers reached a two-year low:
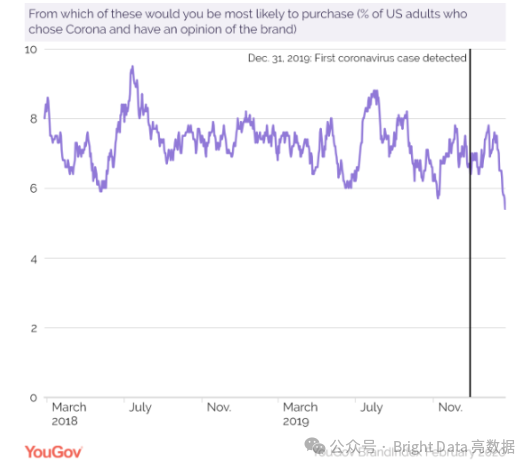
Meanwhile, leading search engine trend finder SEMrush reported a surge in search phrases related to beer and the virus, including “corona beer virus” and “beer coronavirus,” among others. These associations are primarily user-generated, but many experts would not rule out the possibility of Corona beer’s competitors using this negative publicity to dilute a brand that has been on the rise in recent years.
The fact is, brand creation is a long and costly process. The stronger and more profitable your brand, the more it motivates malicious actors to exploit the brand and irreversibly damage everything you and your company have worked hard to create.
As a brand owner, what can you do to protect your brand value and prevent brand theft and dilution?
First, it’s important to understand what brand abuse is. Generally, brand abuse refers to the unauthorized use of your intellectual property, name, logo, reputation, or any other marketable goods you have exclusive legal rights to. As a business owner, you should be familiar with the different types of brand abuse currently prevalent on the internet, including:
Rogue websites are created by malicious third parties who have identified your website (or IP address) as a valuable asset generating high-intent web traffic. Typically, these types of cybercriminals attempt to exploit your digital assets in three ways:
This is a simple yet effective technique using variants of your website domain name to redirect traffic to a site that attempts to “capture” users trying to access your site. A simple example is someone typing “Yaho” instead of “Yahoo.”
In this scenario, a third party might use your brand name and web domain, the only difference being the country it’s registered in. For example, most American companies have “.com” at the end of their web addresses, which is unique to them. But someone could easily use your exact web address and buy the domain in France, for example, using “.fr,” which is the suffix for web addresses registered in France.
This is very similar to “Malicious Domain Creation,” except that the criminal group tries to replicate or clone your website in your home market (e.g., the USA), making consumers believe they are browsing your brand’s “official” website. Copyright Infringement
or piracy is another very common profit-driven criminal activity. Generally, copyrights are granted to artistic works (such as Disney illustrations) or literary works (such as “The Da Vinci Code”), which are created or purchased by your company. In this case, taking Disney as an example, cybercriminals could print Mickey Mouse on merchandise and sell these items online, despite not having the copyrights to these illustrations.
Similar to “Domain Squatting,” trademark squatting typically manifests as registering a version of your trademark that is the same, similar, or a transliteration in a domestic or foreign country. A well-known example is China’s “Tesla.” Chinese businessman Zhan Baosheng was able to legally register the “Tesla” name and the company’s “T” logo without Tesla’s knowledge.

Image from the internet. Chinese businessman Zhan Baosheng sued Tesla, demanding about $3.85 million and asking them to close their showrooms in mainland China, based on his trademark infringement lawsuit.
Now that you have a better understanding of how brands can be harmed by malicious activities, let’s look at the impact of these activities. Here are some of the most common negative effects of brand abuse on companies:
Your brand, logo, and designs mean something. For example, when someone buys a Louis Vuitton bag, they are not just buying a bag, but a lifestyle and a promise of quality. When consumers and suppliers encounter low-quality counterfeits, it lowers the brand’s reputation and consumer trust in the brand. Your brand value is automatically diluted by such activities.
Apart from trust issues, a major and obvious result of brand manipulation is the sharp decline in sales that most businesses experience. Tech-savvy actors might redirect your normal web traffic and offer very similar goods at much lower prices. If you have recently experienced a sharp decline in sales, despite maintaining the same level of marketing activity investment and accompanied by healthy business activity signs, you are likely a victim of brand theft.
Manually combating counterfeiting and brand dilution is a very resource-intensive job. It requires a technical team for keyword, image, and product monitoring, as well as an all-around legal team to fight for you. This “army” requires substantial investment from the brand side.
All of this raises the above question: How can the process of protecting the brand from cybercriminals and malicious actors be elevated to a new level? Here are some best practices you can start implementing today:
Consumers are often unaware of counterfeits, fakes, and intellectual property theft. They honestly believe they are purchasing original goods or registering for your legitimate services. The best tool against ignorance that you can implement is education! Educate your customer base on how to identify imposters, impersonators, and counterfeits. The more educated consumers are, the less likely they are to be deceived by online scams.
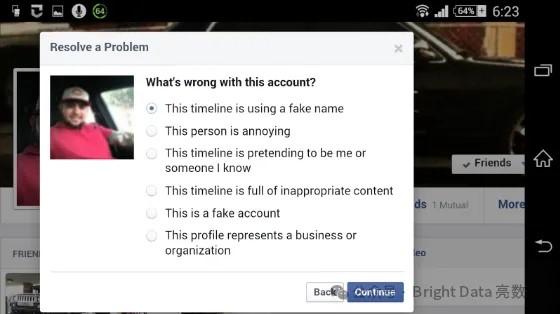
Social media impersonation has also become a hot method for brand imposters. In this case, you need to fight fire with fire. Establish a strong social media presence and report unofficial accounts, profiles, and pages to those responsible for monitoring online social activities.
To successfully maintain control over your intellectual property and enforce IP or content removal, you first need to ensure that your intellectual property is registered through patents and trademarks, otherwise you have no more claim to your intellectual property than the next person. For infringing content and rogue websites, consider purchasing variants of your main domain name, both domestically and internationally. If you have completed all the above steps and identified harmful websites, contact the website administrator and ask them to remove it before taking legal action.
Working with other companies is a business necessity, as is hiring skilled employees with deep industry knowledge and experience. This does not mean you can do without signing confidentiality agreements (NDAs) and non-compete agreements (NCAs). This is a basic and relatively simple way to protect yourself from the attacks you are most vulnerable to, but many businesses overlook these important clauses and contracts in their day-to-day business processes.
Many businesses do not understand the benefits that proxies can bring to their organization in terms of brand protection. They are often not seen as relevant solutions or courses of action. What most people do not know is that many leading brands around the world are using proxies for brand protection services to protect themselves from brand abuse, brand dilution, and other malicious attacks on their brand and ultimately their profits.
Bright Data is a world-leading residential proxy service that helps companies protect their online assets through a global network of over 72 million IPs. A great example is a client of Bright Data who uses our services to track online reviews and rankings on the web, as well as scan the web for negative or misleading brand mentions And. We help them eliminate false information (read: fake news), and provide them and their customers with intelligent alert systems, notifying about misleading search results (i.e., SERP scraping against malicious websites), domain abuse, and illegal product displays (e.g., scraping eBay and Amazon for counterfeits).
According to records and debates in the U.S. Congress, piracy has become a billion-dollar industry operated by highly sophisticated criminals. Using millions of real residential and mobile IP addresses, you will appear as a regular customer when scanning the web, allowing you to detect these fraudsters. Thus, you can expose the “real” information shown by the smearers. This helps automate and simplify the process of identifying entities that devalue your brand and product offerings.
The digital age has provided many new opportunities for brands and businesses. However, the same technological advancements available to legitimate businesses also provide opportunities for hackers, cybercriminals, and illegal entities trying to profit from the hard-built brand and brand recognition.
Click https://get.brightdata.com/duoplus to utilize data-driven brand intelligence and protect your intellectual property today.
Article source: Bright Data.

Introduction: In this new era of rapid change, every small shift can lead to new trends in the industry. DuoPlus Cloud …

DuoPlus Cloud Smartphone leads the technological trend, powered by Android 15 online! Specially designed for …
No need to purchase multiple real phones.
With DuoPlus, one person can operate numerous cloud phones and social media accounts from a single computer, driving traffic and boosting sales for you.
